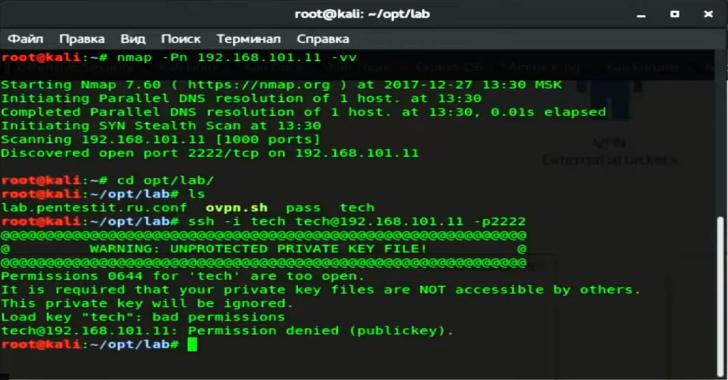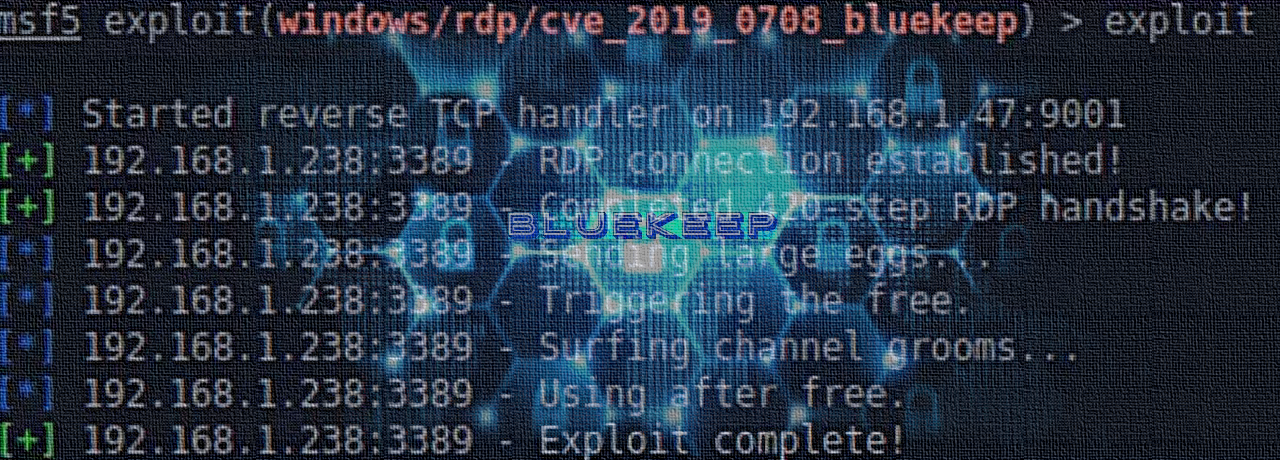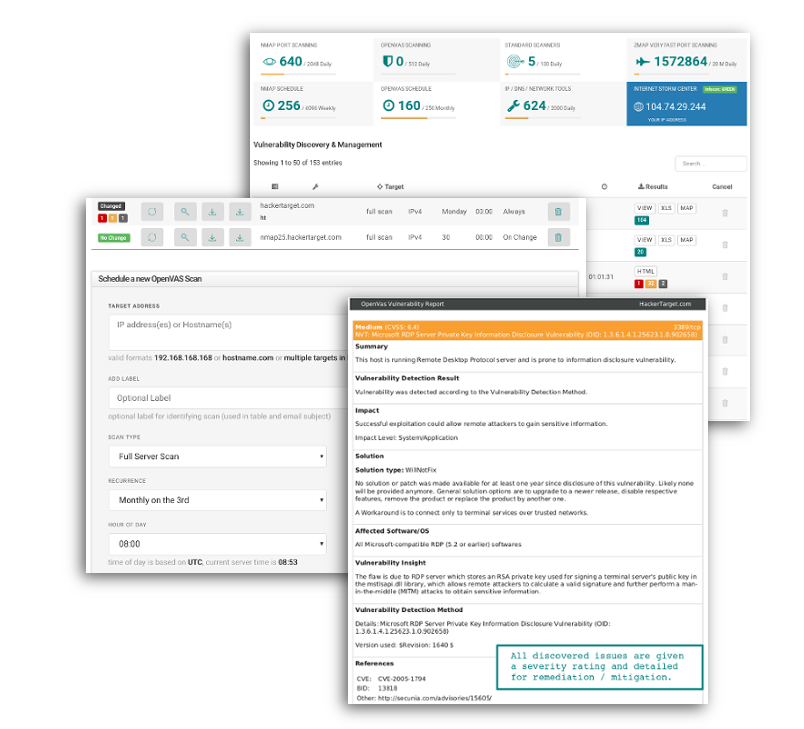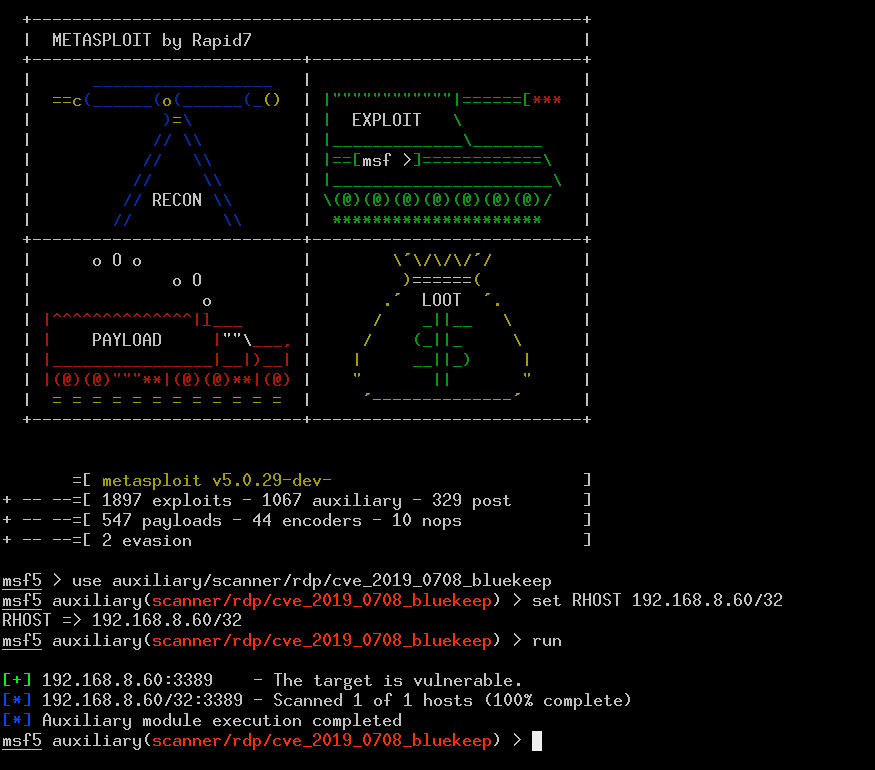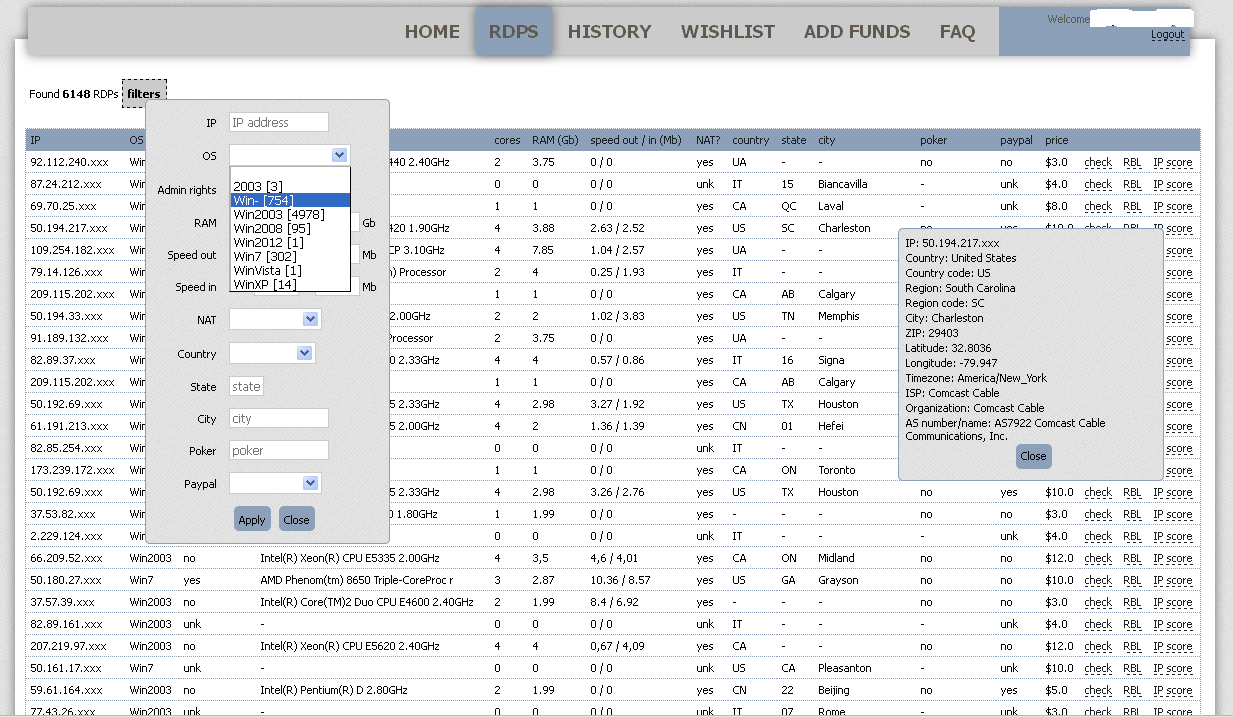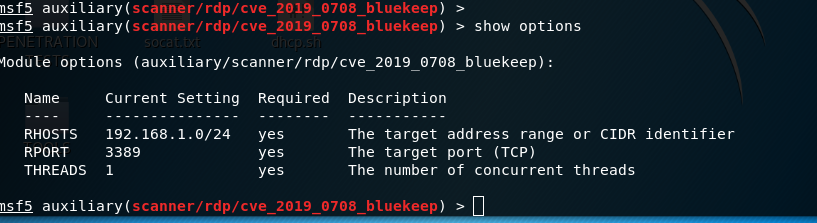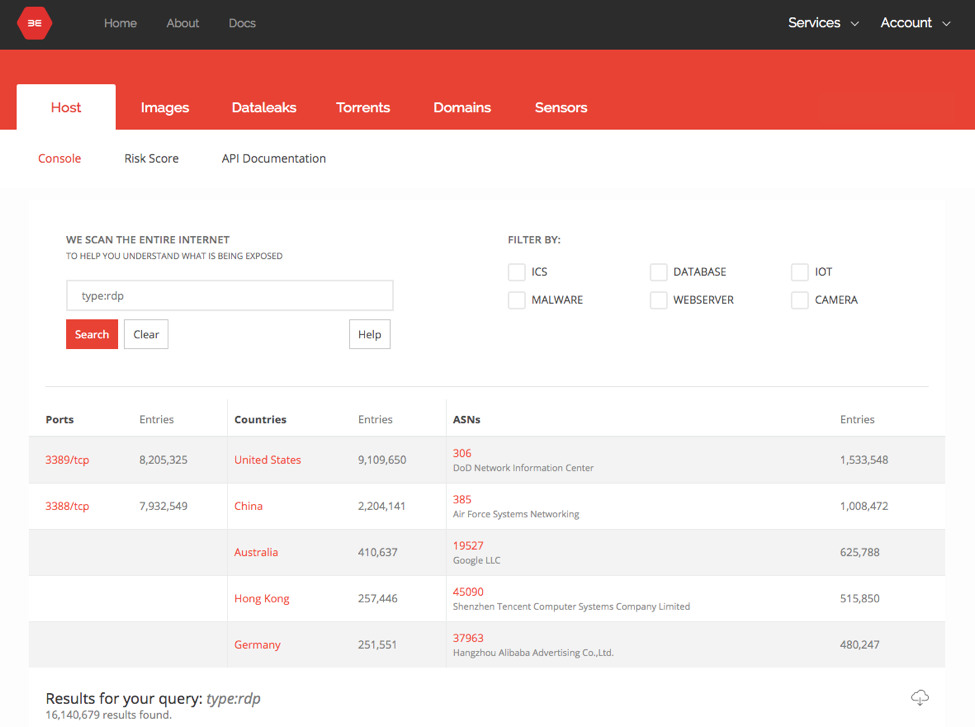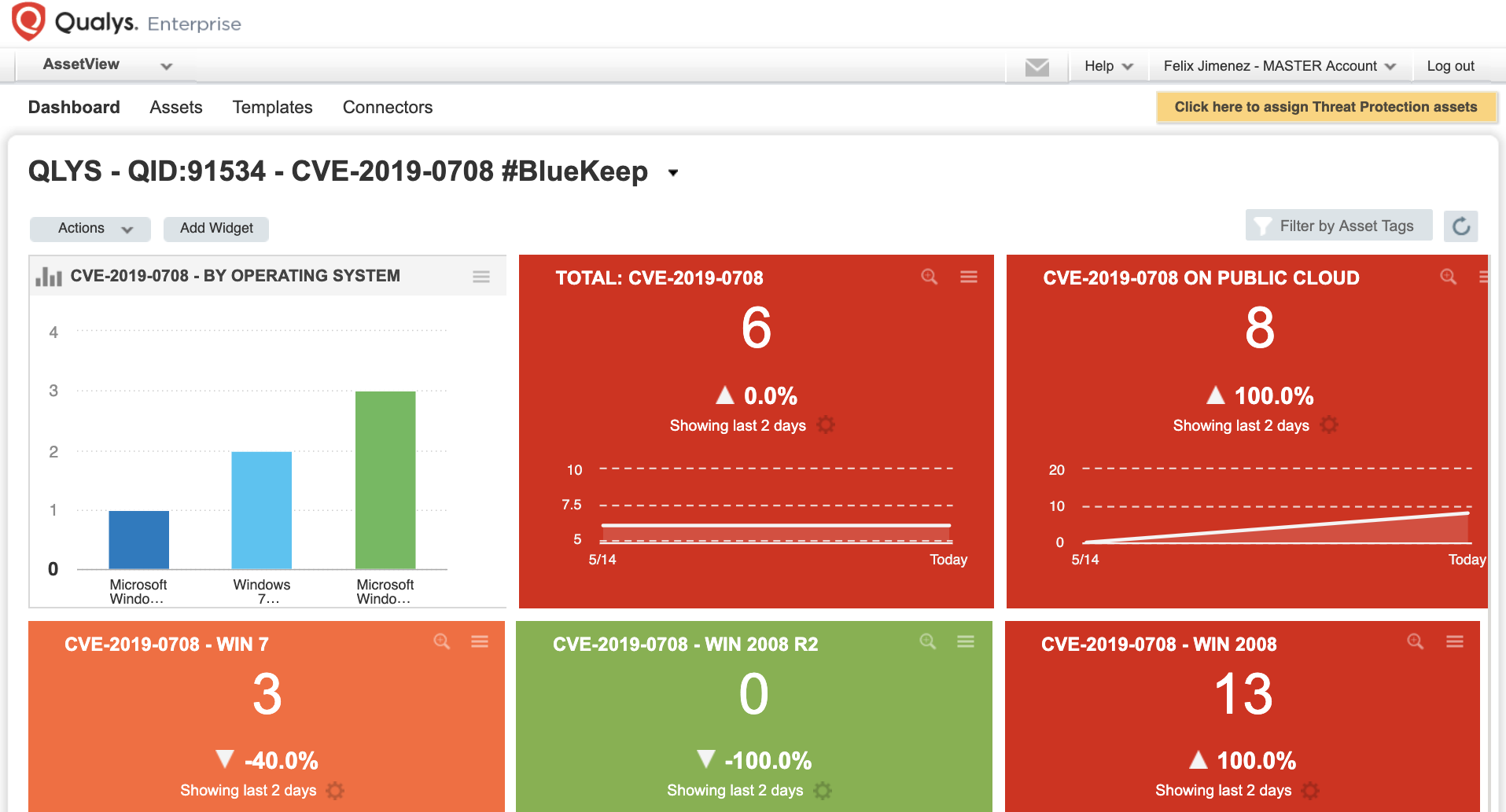
Windows RDP Remote Code Execution Vulnerability (BlueKeep) - How to Detect and Patch | Qualys Security Blog

Microsoft works with researchers to detect and protect against new RDP exploits - Microsoft Security Blog

Microsoft works with researchers to detect and protect against new RDP exploits - Microsoft Security Blog